Explain the Major Difference Between Wpa-psk and Wpa-enterprise
WPA-EnterpriseEAP is like having an key card system that. CCMP replaces WPAs TKIP.

Wi Fi Security Evolution How We Ended Up In Wpa3
However WPA is still vulnerable because it is based on the RC4 stream cipher.

. WPA has discrete modes for enterprise users and for personal use. Explain the differences between WEP WPA WPA2 RSN and AES. Data integrity is provided through CRC 32.
WPA2 is more difficult or. In addition depending on your router performance can slow down by 30 percent or more when enabling WEP or WPA. 2WPA only supports TKIP encryption while WPA2 supports AES.
To use an analogy WPA-PSK is like having a dead bolt on your company door and providing every employee the same key. Simplifying WPA2-Enterprise and 8021x. Similar to WEP a static key or passphrase is set but WPA-PSK uses TKIP.
The major difference between WPA2 and WPA is that WPA2 improves the security of a network because it requires using a stronger encryption method called AES. 1WPA2 is the improved version of WPA. Textbook Solutions Expert Tutors Earn.
The PSK that you see with WPA2 and WPA is basically the wireless network key that you have to enter when connecting to a wireless network for the first time. The keys used by WPA are 256-bit a significant increase over the 64-bit and 128-bit keys used in the. WPA-Personal is a common method to secure wireless networks and it is suitable for most home networks.
Use at docx from IS MISC at IIPM. The main difference between WEP and WPA is that WPA adds an extra security protocol to the RC4. WPA may be hackable while WPA2 and WPA3 is not.
WPA3 includes some important upgrades for. Authentication method in WPA is WPA-PSK and WPA-Enterprise. The most common WPA configuration is WPA-PSK Pre-Shared Key.
Data integrity is provided through Message integrity code. WPA-PSK automatically changes the keys at preset intervals to make it difficult for hackers to find. Main Differences Between WPA and WPA2.
WPA2-PSK is a hardware security module whereas WPA-PSK is a software security module. WPA-Enterprise provides the security needed for wireless networks in business. Most modern WPA applications use a pre-shared key PSK most often referred to as WPA Personal and the Temporal Key Integrity Protocol or TKIP tiːˈkɪp for encryption.
4 Explain the difference. Unlike WEP and WPA WPA2 uses the AES standard instead of the RC4 stream cipher. Following are the features of WPA Wi-Fi Protected Access.
WPA provides assurance to users of wifi network that their data remains protected and only authorized persons are using the wifi. WPA2-PSK uses modern security standard WPA2 along with TKIP or AES. As with WEP WPA reduces the processing power of the network device.
WPA-Personal is a common method to secure wireless networks and it is suitable for most home networks. WPA2-Enterprise has been around since 2004 and is still considered the gold standard for wireless network security delivering over-the-air. View Explain the differences between WEP WPA WPA2 RSN and AES.
The enterprise mode WPA-Extensible Authentication Protocol WPA-EAP uses more stringent 8021x authentication. WPA2 provides a stronger security system than that of WPA. WPA2 has stronger security and is easier to configure than the prior options.
The main difference with WPA2 is that it uses the Advanced Encryption Standard AES instead of. WPA-Enterprise provides the security needed for wireless networks in business environments where a RADIUS server is deployed. 128-bit encryption in WPA3-Personal mode 192-bit in WPA3-Enterprise.
3Theoretically WPA2 is not hackable while WPA is. WPA2 is securer than WPA and is currently used by most WiFi networks. WPA uses TKIP whereas WPA2 uses AES.
Use at least three.

Comparison Between Wep Wpa And Wpa2 Download Table
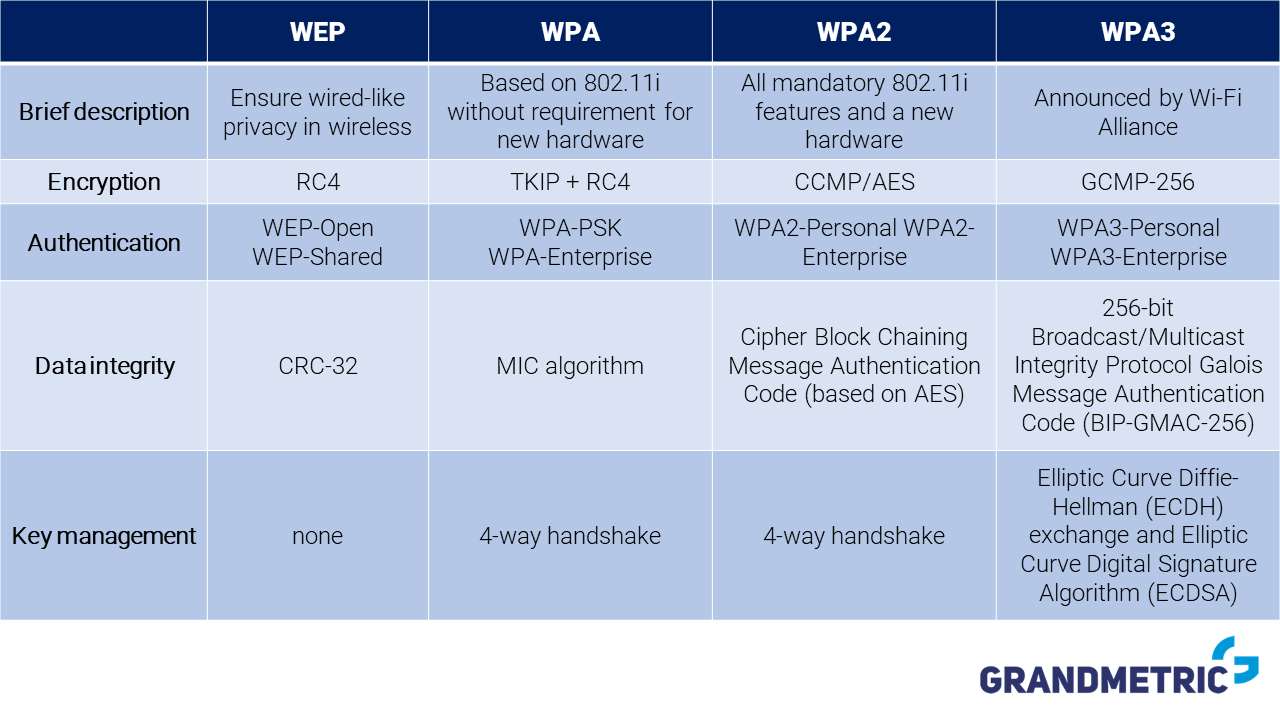
Wi Fi Security Evolution How We Ended Up In Wpa3


No comments for "Explain the Major Difference Between Wpa-psk and Wpa-enterprise"
Post a Comment